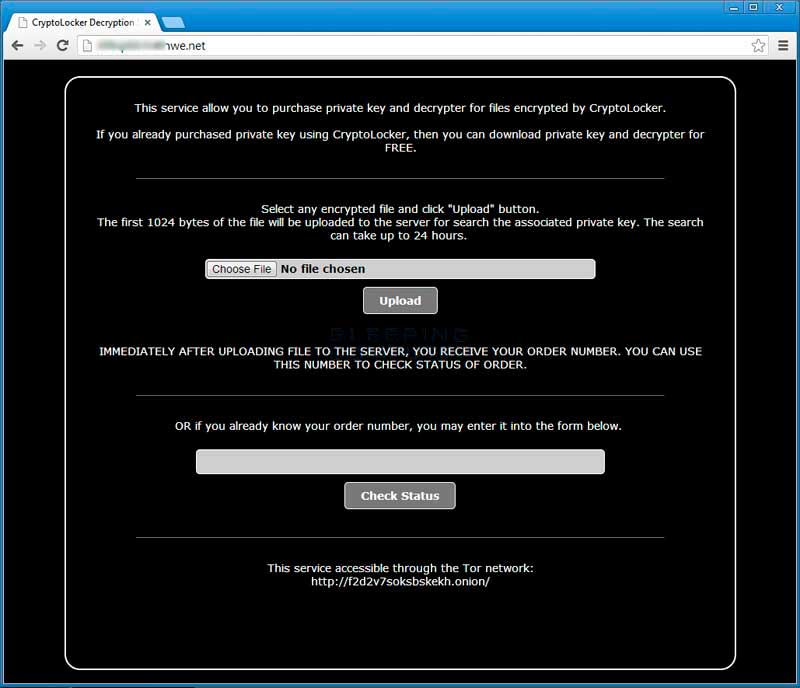
For those users who are affected by CryptoLocker and did not have a backup, trying to pay the ransom has been a difficult process. This is because antivirus programs remove the infection or the registry key that is required to pay the ransom and decrypt the files. It appears that the malware developers were listening, as they have now implemented a decryption service that is designed to look like a customer support site. This service is available by connecting directly to a Command & Control server's IP address or hostname or through Tor via the f2d2v7soksbskekh.onion/ address.
Infected users can use this service to upload a CryptoLocker encrypted file and have your "order" looked up. If your order is found, it will display the date that your computer was infected and your public key. It will then prompt you to purchase the private key by sending 10 bitcoins or approximately $2,120 USD. Once a payment is made it must have 10-15 bitcoin confirmations before your private key and a decrypter will be made available for download. They further state that if you have previously paid the ransom, they will provide the private key and decrypter to you for free.
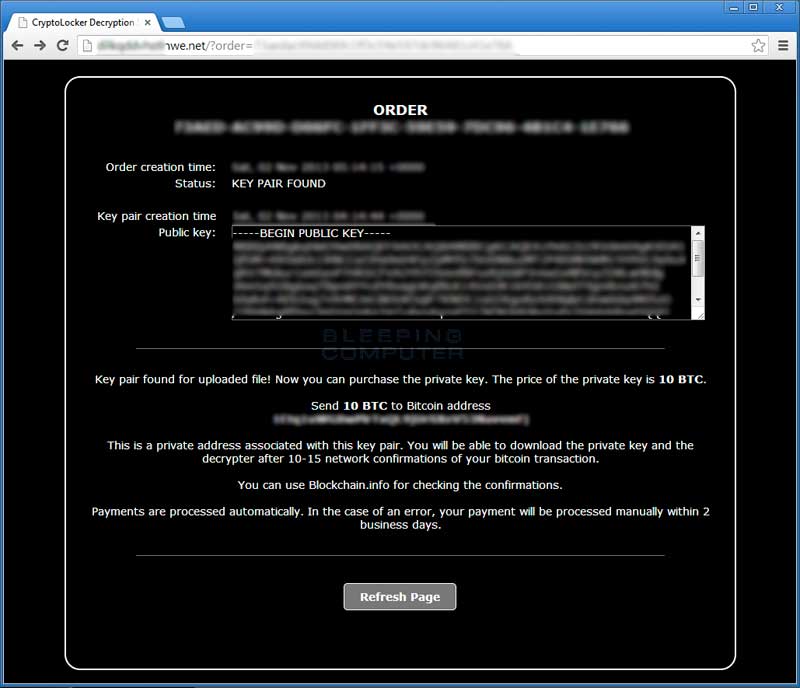
In the past, users were able to use the main CryptoLocker program to decrypt their files by paying 2 bitcoins. If an AV program deleted the infection, as long as they had the required registry key, they could download the infection as a file called 0388.exe and run it again to pay the ransom. At this time, the 0388.exe files are now longer available for download. Due to this, it is unsure as of yet if this new decryption service, and the price of 10 bitcoins, will become the new cost decryption if the infection is removed.
More information about this infection can be found in the CryptoLocker Ransomware Information Guide and FAQ.
Update: 11/4/2013:
The decryption service now still allows you to pay 2 bitcoins during your normal 3 day timer period. After that period, the price increases to 10 bitcoins.





 Back to top
Back to top









