
Google has fixed another zero-day vulnerability in the Chrome browser, which was exploited by security researchers during the Pwn2Own hacking contest last month.
Tracked as CVE-2024-3159, this high-severity security flaw is caused by an out-of-bounds read weakness in the Chrome V8 JavaScript engine.
Remote attackers can exploit the vulnerability using crafted HTML pages to gain access to data beyond the memory buffer via heap corruption, which can provide them with sensitive information or trigger a crash.
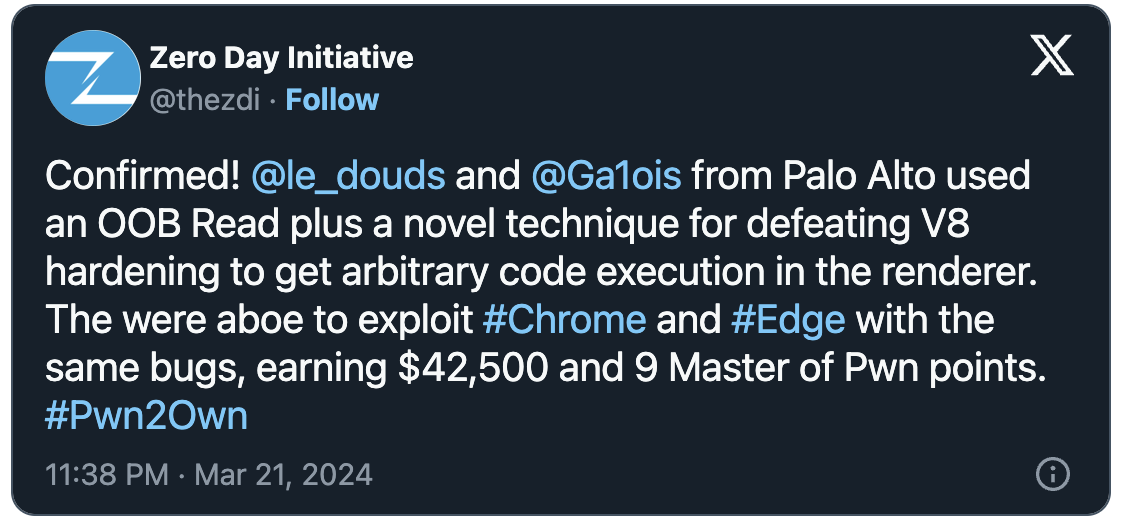
Palo Alto Networks security researchers Edouard Bochin and Tao Yan demoed the zero-day on the second day of Pwn2Own Vancouver 2024 to defeat V8 hardening.
Their double-tap exploit allowed them to execute arbitrary code on Google Chrome and Microsoft Edge, earning them a $42,500 award.
Google has now fixed the zero-day in the Google Chrome stable channel version 123.0.6312.105/.106/.107 (Windows and Mac) and 123.0.6312.105 (Linux), which will roll out worldwide over the coming days.
One week ago, Google fixed two more Chrome zero-days exploited at Pwn2Own Vancouver 2024. The first, a high-severity type confusion weakness (CVE-2024-2887) in the WebAssembly (Wasm) open standard, was targeted by Manfred Paul's double-tap RCE exploit that targeted both Chrome and Edge.
The second, a use-after-free (UAF) weakness in the WebCodecs API (CVE-2024-2886), was also exploited by KAIST Hacking Lab's Seunghyun Lee to gain remote code execution on both Chromium web browsers.
Mozilla also patched two Firefox zero-days exploited by Manfred Paul at this year's Pwn2Own Vancouver competition on the same day the bugs were exploited.
While both Google and Mozilla released security patches within a week, vendors usually take their time to fix Pwn2Own zero-days since Trend Micro's Zero Day Initiative publicly discloses bug details after 90 days.
In total, Google patched four Chrome zero-days this year, with the fourth addressed in January as an actively exploited zero-day (CVE-2024-0519) that enabled attackers to crash unpatched browsers or access sensitive information due to an out-of-bounds memory access weakness in the V8 JavaScript engine.
On Tuesday, the company also fixed two Android zero-days exploited by forensic firms to unlock Pixel phones without a PIN and gain access to the data stored within them.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now