A new ransomware has been discovered called Locky that encrypts your data using AES encryption and then demands .5 bitcoins to decrypt your files. Though the ransomware sounds like one named by my kids, there is nothing childish about it. It targets a large amount of file extensions and even more importantly, encrypts data on unmapped network shares. Encrypting data on unmapped network shares is trivial to code and the fact that we saw the recent DMA Locker with this feature and now in Locky, it is safe to say that it is going to become the norm. Like CryptoWall, Locky also completely changes the filenames for encrypted files to make it more difficult to restore the right data.
At this time, there is no known way to decrypt files encrypted by Locky. For those who wish to discuss this ransomware or have questions, please feel free to post in our Locky Ransomware Support and Help Topic.
Locky installed via fake invoices
Locky is currently being distributed via email that contains Word document attachments with malicious macros. The email message will contain a subject similar to ATTN: Invoice J-98223146 and a message such as "Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice". An example of one of these emails can be seen below.

Attached to these email messages will be a malicious Word document that contains a name similar to invoice_J-17105013.doc. When the document is opened, the text will be scrambled and the document will display a message stating that you should enable the macros if the text is unreadable.

Once a victim enables the macros, the macros will download an executable from a remote server and execute it.

The file that is downloaded by the macro will be stored in the %Temp% folder and executed. This executable is the Locky ransomware that when started will begin to encrypt the files on your computer.
Locky encrypts your data and completely changes the filenames
When Locky is started it will create and assign a unique 16 hexadecimal number to the victim and will look like F67091F1D24A922B. Locky will then scan all local drives and unmapped network shares for data files to encrypt. When encrypting files it will use the AES encryption algorithm and only encrypt those files that match the following extensions:
.mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11 (Security copy), .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key, wallet.dat
Furthermore, Locky will skip any files where the full pathname and filename contain one of the following strings:
tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows
When Locky encrypts a file it will rename the file to the format [unique_id][identifier].locky. So when test.jpg is encrypted it would be renamed to something like F67091F1D24A922B1A7FC27E19A9D9BC.locky. The unique ID and other information will also be embedded into the end of the encrypted file.
It is important to stress that Locky will encrypt files on network shares even when they are not mapped to a local drive. As predicted, this is becoming more and more common and all system administrators should lock down all open network shared to the lowest permissions possible.
As part of the encryption process, Locky will also delete all of the Shadow Volume Copies on the machine so that they cannot be used to restore the victim's files. Locky does this by executing the following command:
vssadmin.exe Delete Shadows /All /Quiet
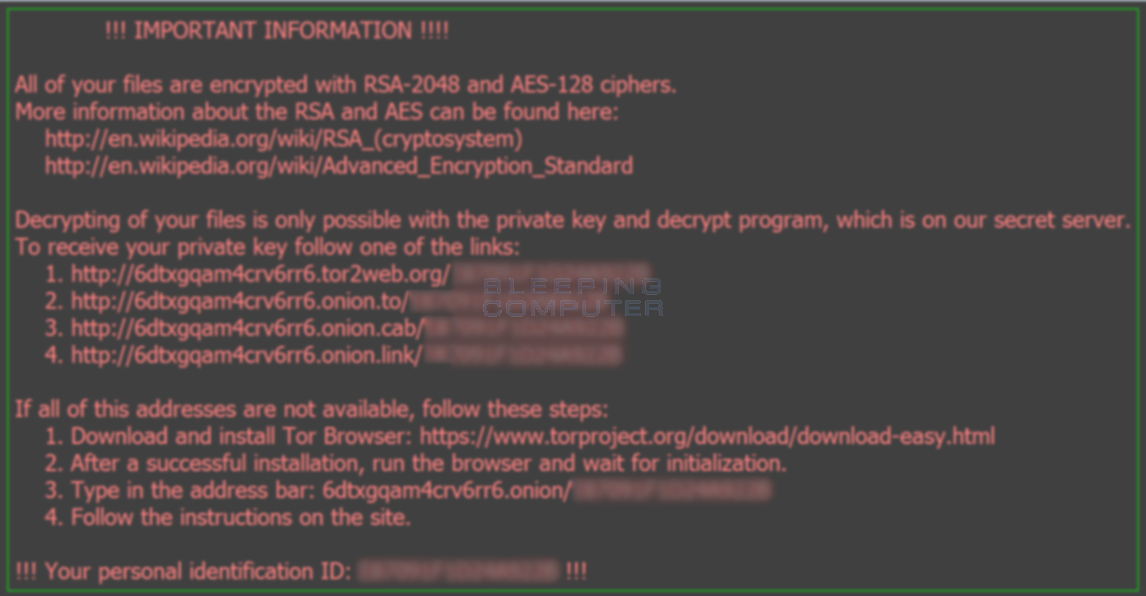
In the Windows desktop and in each folder where a file was encrypted, Locky will create ransom notes called _Locky_recover_instructions.txt. This ransom note contains information about what happened to the victim's files and links to the decrypter page.
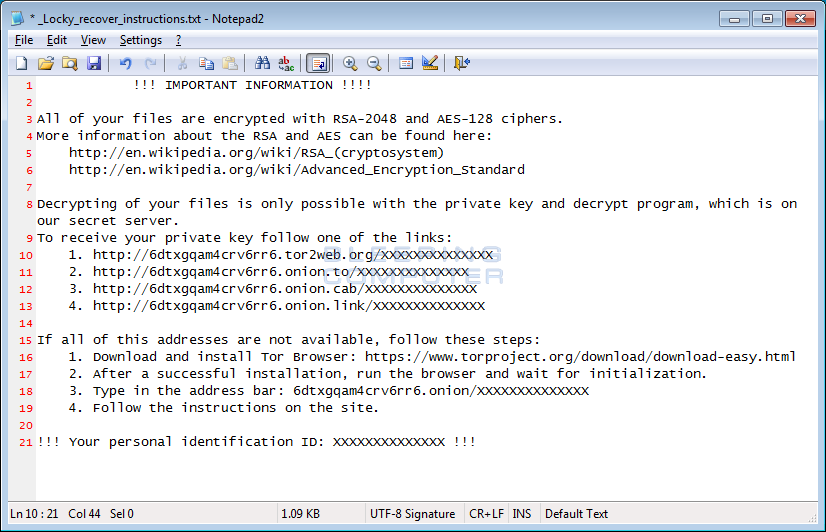
Locky will change the Windows wallpaper to %UserpProfile%\Desktop\_Locky_recover_instructions.bmp, which contains the same instructions as the text ransom notes.
Last, but not least, Locky will store various information in the registry under the following keys:
- HKCU\Software\Locky\id - The unique ID assigned to the victim.
- HKCU\Software\Locky\pubkey - The RSA public key.
- HKCU\Software\Locky\paytext - The text that is stored in the ransom notes.
- HKCU\Software\Locky\completed - Whether the ransomware finished encrypting the compute.r
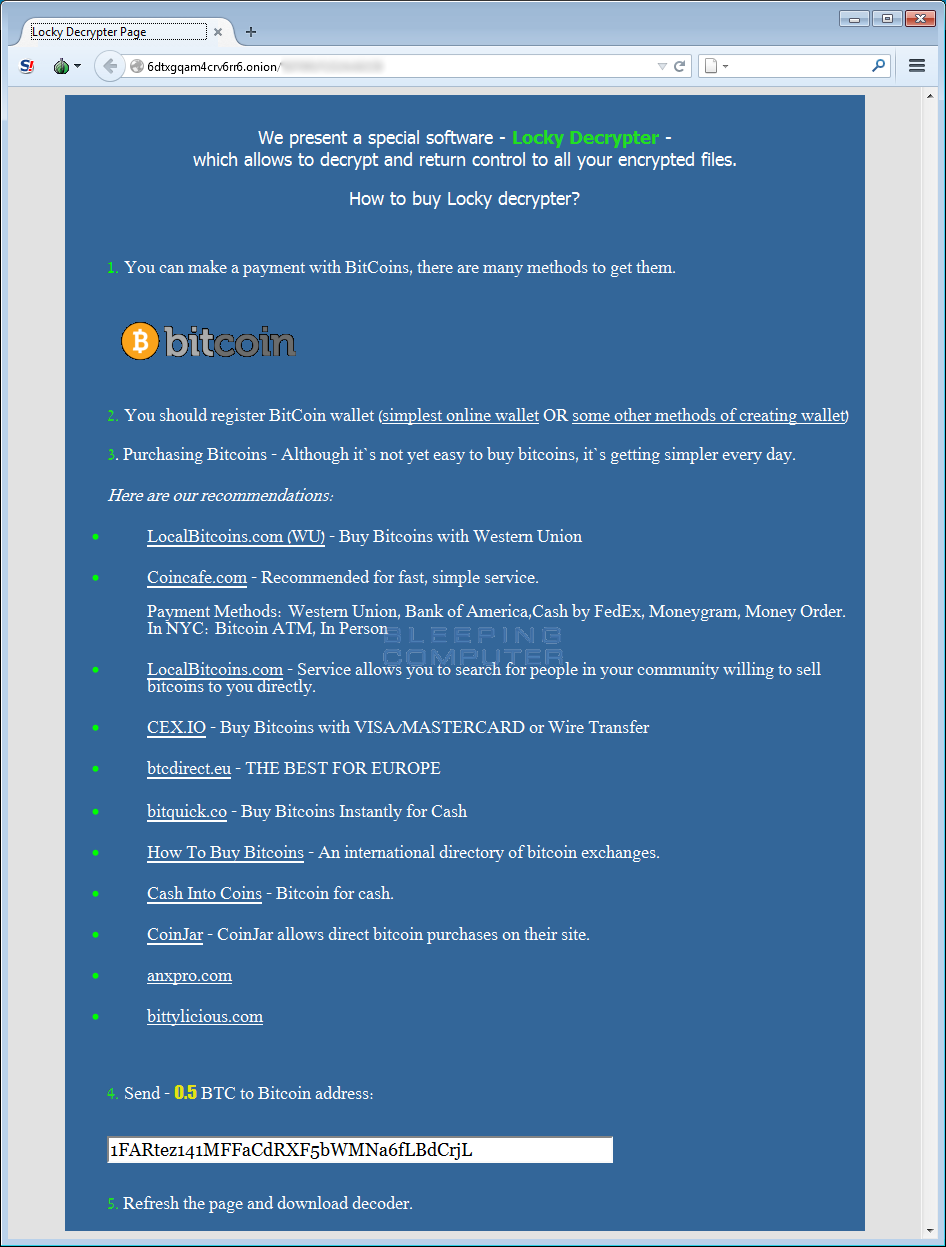
The Locky Decrypter Page
Inside the Locky ransom notes are links to a Tor site called the Locky Decrypter Page. This page is located at 6dtxgqam4crv6rr6.onion and contains the amount of bitcoins to send as a payment, how to purchase the bitcoins, and the bitcoin address you should send payment to. Once a victim sends payment to the assigned bitcoin address, this page will provide a decrypter that can be used to decrypt their files.
Locky related Files
%UserpProfile%\Desktop\_Locky_recover_instructions.bmp
%UserpProfile%\Desktop\_Locky_recover_instructions.txt
%Temp%\[random].exe
Locky related Registry entries
HKCU\Software\Locky
HKCU\Software\Locky\id
HKCU\Software\Locky\pubkey
HKCU\Software\Locky\paytext
HKCU\Software\Locky\completed 1
HKCU\Control Panel\Desktop\Wallpaper "%UserProfile%\Desktop\_Locky_recover_instructions.bmp"


Comments
InsufficientFunds - 8 years ago
I really admire how they disregard all the temporary files and rubbish Windows leaves behind. That's the funny part.
I would like to also add that it temporary creates an "svchost.exe" process with the Description "svchost.exe" while it encrypts all your files then deletes itself from the system.
DouglasL - 8 years ago
Will it attack hidden shares?
Lawrence Abrams - 8 years ago
No, it does not.
Freakish84 - 8 years ago
Hi all!
I got this "F.C...G" virus... :(
Since 1 day ago i got an email for a MicrosoftOffice Invoice wit a word attachments.
I opened and the virus was work, my nod 32 did not see anything.
And the biggest problem was that, to my OneDrive was synchronized!!! :O
Anyone heard about any solution, cos my backup was my OneDrive, and hetese files was so important for me about my work...
Demonslay335 - 8 years ago
You can try this article for restoring previous versions of OneDrive. Otherwise, you can try the usual recovery tools like Recuva, ShadowExplorer, and PhotoRec. Full analysis seems to be still pending on the extent of the damage done by this variant.
https://support.office.com/en-us/article/Restore-a-previous-version-of-a-document-in-OneDrive-for-Business-159cad6d-d76e-4981-88ef-de6e96c93893
Freakish84 - 8 years ago
I found that solution on the internet, but i did not find the option in the OneDrive account...
I contact the support, and they are so mean, and did not understand to i like make that u shown me :D
Are there any decryption solution, or will there any?
Demonslay335 - 8 years ago
Do you pay for OneDrive at all, or just the free storage? I would definitely complain if they were rude to you, ask to speak to a manager. That is just terrible business practice either way... The analysts are still taking a look at this one, so there is no word on whether it will be decryptable. There is rarely any way of seeing immediately how long it will take to find a solution. We just have to wait for the full assessment. Since it has not been cracked within the first few days, we can only assume it isn't an easy one with a very simple slip-up, but we cannot gauge if it can be done yet.
wiza - 8 years ago
My computer has been infected. I encriptaron files and leave you with extension. Locky.
I appreciate any guidance !
ezshi87 - 8 years ago
One of my clients got hit with this virus this morning. Is there any way to tell where this came in, which computer this started on? I already stopped all network shares, scanned all servers and PCs. I want to know once we get all the files back that the virus is gone and doesn't come back and infect us again. And I mean this specific virus ID on my network. I know this virus can hit us again from another source but I mean this specific Locky virus currently on my network.
Gonna be a loooooong day! Thanks!!
ultramagnes23 - 8 years ago
you can right-click on the recovery instructions -> properties -> security -> advanced -> owner
the owner will tell you who the culprit is. this will not work if you use a workgroup share with just one user account, but very effective in a domain.
EDIT: I'm recovering a customer with this now. They use Workgroup but luckily everyone had their own login to the workgroup 'server'. The culprit was the receptionist who was coincidentally looking through her email for an invoice...
jjmanthei05 - 8 years ago
The way we found where it started from was we looked at the created by login on the ransom text file placed in each directory. the encrypted file will show created by whoever created the original file but since the ransom text files are new that should narrow down your user.
FrankysWeb - 8 years ago
There is a way to protect Windows Fileservers:
https://www.frankysweb.de/windows-fileserver-vor-ransomware-crypto-locker-schuetzen/
(German language)
Ikkegoemikke - 8 years ago
We were attacked tuesday by this ransomware. 150 Emails spoofed to our mailserver. 149 Mails were blocked by the Barracuda spamfilter. One slipped through and was initialised by a coworker from the saledepartment. In half an hour our fileserver, applicationserver and shared maps on local PC's was encrypted.
After locating the PC where it all started, we took that one from the network and started to restore everything from the backup. In one hour the fileserver and applicationserver was back working.
Except one local folder with lots of data in that wasn't on the fileserver was completely destroyed. We succeeded in fixing this as follows.
First we installed RECUVA on this PC and tried to recover the lost map.The fact that the user kept working on it, had as result that most files were'nt recoverable because they were overwritten by cookies and temporary internetfiles. (So when noticing the LOCKY files ... stop working)
Windows 7 has shadow files. Too bad those files are corrupt because of the LOCKY virus ... but ... we were able to recover those files with RECUVA, restore them and start SHADOWEXPLORER and go back 6 days to recover a shadowcopy from the lost data folder. In the end we recovered about 99% of lost files !
But as someone said before .... nothing helps to prevent it so backup, backup and backup .....
Lawrence Abrams - 8 years ago
That's great news. So to be clear, you use recuva to restore an old SVC and then used that to restore the files?
Knet - 8 years ago
Once my laptop is infected (for example at home), will Locky infect further data when I connect my laptop to a domain (at work, with mapped drives for example)?
Demonslay335 - 8 years ago
Most likely, if the virus is still active. Make sure to properly cleanup the computer and update all software before connecting it to anything. I would almost even wipe the computer if you are going to connect to a corporate network. Be sure to backup your encrypted files in the event of a breakthrough in decryption in the future.
chisel954 - 8 years ago
-breakthrough....?
are " who? " actually working on breaking decryption for these ransom programs? That's cool to know!
Demonslay335 - 8 years ago
This is the advice we give everyone affected by ransomware. What seems to be impossible to decrypt today, always has a chance of being decrypted in the future. This is not to say this will happen for all ransomwares, but it has happened a few times before. It is always best to backup all of your files and hope for the future. Even better, if you can, is to make an image of the system and archive that; since the full analysis of this particular ransomware has not been released, we do not know what may be of use yet if a solution is found.
There are a few security firms who are looking at this as far as I have heard. I believe Emsisoft is currently looking into it, as is an Italian security firm I've talked with.
k-gsp - 8 years ago
Please, if somebody was able to decrypt a locky files, could help me with a solution?
Demonslay335 - 8 years ago
There is no way to decrypt Locky at the current time. It is best to backup your data and hope for the future.
Tech_Dude - 8 years ago
Is Locky found only .DOC files or does it also contained in .DOCX files? Are there any other extensions to watch?
frankploegmakers - 8 years ago
You find a list above ....
Simple do a search on the computer; *.locky and you find them all.
:)
Tech_Dude - 8 years ago
That didn't answer my question and wasn't what I asked.
Lawrence Abrams - 8 years ago
I believe it can be both.
Demonslay335 - 8 years ago
It could be delivered as either .doc or .docx, but I would guess it is most commonly .doc files, since older versions of Office and the Office file format have more exploits. I would prepare for both, or just any Office document in general that asks to run macros.
vilhavekktesla - 8 years ago
Hi, I got a virus thoug email yesterday. I have not investigated it heavily yet. Something tells me it is locky. My case was this. One spam address send email to my private mail. Mail sent as admin meaning me, so basically from me to me... Then no content except one attachement
Abot 3 kB. the attachment was one zip, inside the zip one javascript with pretty amusing content, not similar to the word-macro example above.
I still have the virus, bot in my mail, as a zipped file, as a zipped and encrypted file. I sent the virus to BC for analysis, I have also posted it on Virustotal. The word locky is mentioned on Virustotal.
The virus was not active on my computer, since I did not fire up the javascript. So to answer your question. Yes as doc, and of course docx which is simply a .zip with a special name and with xml-content, yes as .zip and probably also as .js and if anoyone want to it could also be a .pdf hoping for that your Acrobas runs javascript without asking. I have some speculations now, but .zip and .doc is already confirmed, so .js, and .pdf is simply a matter of virus makers creativity.
Regards
reginaldvw - 8 years ago
Please see the list in "Locky encrypts your data and completely changes the filenames". It will encrypt all the file types listed there.
peej228 - 8 years ago
I created a program to detect missing or modified files in a windows file share caused by Ransomware .
http://www.questiondriven.com/2016/02/18/beta-testing-for-ransomware-detection-in-file-share/
vilhavekktesla - 8 years ago
Care to tell me more about your program in pm?
I'm thinking of evaluating your program thoughts.
Are anoyone other familier with this?
http://www.questiondriven.com/2016/02/18/beta-testing-for-ransomware-detection-in-file-share/
frankploegmakers - 8 years ago
We did receive the locky virus.... (as described above....attachment on a email, WORD ....)
Antivirus did not detect anything....
We had damage in 45 minutes on 200.000 files.....
Stopping the virus and removing was not so difficult; see info above.
restoring the enormous amount was a lot of work so we decided to pay (in this case 1 bitcoin about 400 dollar.... )
No use; as good criminal behaving; take the money and run.
So;
* don`t pay. No use, money will be gone.
* have the best backups you can have... use any cheap storage, but do it. make backups.
* be careful, the best antivirus is totally free, right there; it is on the chair, between the screen and the back of the chair. It is called "user" ....
* So don`t open this nonsense.... Please.
eksihasan - 8 years ago
Hi everyone, We have actually developed a product against cryptolocker and its variants. So far it works perfectly against cryptolocker(last couple versions that we were able to test).
Please take a look at the article here and provide your feedback.
http://www.secpedia.com/reviews/ioaudit-cryptolocker/
vilhavekktesla - 8 years ago
Same to you. Care to tell me more about this in a pm?
... Please take a look at the article here and provide your feedback.
http://www.secpedia.com/reviews/ioaudit-cryptolocker/
...
eq2675 - 8 years ago
Just got my first email with the Locky ransomware. It was a double zipped file, with the final file being named report.226915422.js
Playing with it on my Chromebook, so I should be safe.
Worse part is only 1 anti virus shows it as positive at VirusTotal.com
https://www.virustotal.com/en/file/cbd9e9038bf5959e134ee55ebd6b8c802ee56c54d987a85441f33b361be3ace2/analysis/1456864156/
eq2675 - 8 years ago
Now there are 8 positives at virustotal.com for this file, but Microsoft scans still comes up with a safe results, even after I submitted a sample to the Microsoft Malware Protection Center on 03/01
https://www.virustotal.com/en/file/cbd9e9038bf5959e134ee55ebd6b8c802ee56c54d987a85441f33b361be3ace2/analysis/1456974969/
eq2675 - 8 years ago
Microsoft sent me an email confirming that my submission was infected with the TrojanDownloader:JS/Swabfex.P virus. That's 4 days after my submission. The Microsoft definitions on virustotal.com still shows it as a safe file at the moment, but now 23 of 54 av find this file infected.
https://www.virustotal.com/en/file/cbd9e9038bf5959e134ee55ebd6b8c802ee56c54d987a85441f33b361be3ace2/analysis/
3J Kernel - 8 years ago
Could locky ransomware be decrypted by Tesladecrypt?
I ask that because it uses AES encryption...
Lawrence Abrams - 8 years ago
No. No current flaw in locky's encryption algo.
3J Kernel - 8 years ago
?
fezir108 - 8 years ago
How exactly is it able to enumerate unmapped network drives?
Lawrence Abrams - 8 years ago
Uses the WNetOpenEnum function.
Joe_BubbA - 8 years ago
Hmmm, can Group Policy be used to block use of WNetOpenEnum?
Lawrence Abrams - 8 years ago
Not that I am aware of. Doing so would severely break Windows networking.
nkarafo - 8 years ago
@Ikkegoemikke
So, what is the correct order to achieve the correct restoration of the files?
First you use shadow explorer, you back some days ago and then you use recuva to restore the files OR
first you use recuva to restore the files that you want and go back the file structure with shadow explorer ? And how can this be achieved ? The restored files where should be kept to be fully recovered?
Can you please explain the steps in more detail ?
Thank you !!!!
Lawrence Abrams - 8 years ago
Shadow volumes are deleted, but you can try and restore a shadow volume copy using recuva and then restore from that. I personally have no experience with doing this, but I know people who have done. Will see if I can get more info.
BlazeAxtrius - 8 years ago
What I did after I got infected yesterday. Was to download the shadowexplorer and it pretty much recovered 90% of my lost files.
PS: 90% of them are corrupted
Ikkegoemikke - 8 years ago
Sorry it took me a while. Been busy. But I'll try to explain what we did. First of all you should check if the shadow volumes files still are OK. Locky mostly corrupts those too. What we did is restore the System Volume Information folder (normally that's where the shadow copies are stored). You can see that folder after disabling the "Hide protected operating system files (Recommended)" option in mapoptions. Now we recovered that folder via Recuva. And after that you try to recover the files from the shadow copy. Worked for us !
Ikkegoemikke - 8 years ago
@nkarafo
Sorry for the late reply !
pctechjbay - 8 years ago
I used ShadowExplorer 9.0 on a flash drive. I removed the infected drive and put it in a second computer with no network access (unplugged the CAT5 cable). I ran ShadowExplorer and was lucky that the latest shadow volume was intact and appeared unaffected. I exported the files to a different drive.
cesarfreitas - 8 years ago
Hello guys!
I'm sorry to bother, but can you help me with Shadow Explorer?
I already executed Recuva and was able to restore some shadow files. The problem is, when I run Shadow Explorer, it apparently shows only the C: drive dated 23/03, when we first had the problem...
I recovered the files today... How can I force Shadow Explorer to show these files I recovered?
I couldn't find it anywhere...
Thanks in advance!
eq2675 - 8 years ago
This is getting to be unbelievable. Another attachment infected with Locky and only ONE anti virus is detecting it
https://www.virustotal.com/en/file/a2e9cf7245c0e5d495986d887144f17fd30628ab3dfa37439764413415d64b0a/analysis/1457362291/
eq2675 - 8 years ago
OMG, my submissions of suspected viruses to the Microsoft Malware Protection Center, https://www.microsoft.com/en-us/security/portal/submission/submit.aspx may be paying off.
Just got another suspect email with attachment and ran it at virustotal.com. Only 3 positive detections, but one of them was now Microsoft !!!!!!!!!
https://www.virustotal.com/en/file/ff7a9ad62f4e3670b6ef304e9f624dce2ed4181b61db19016fc88d1cae067b7b/analysis/1457461353/
vilhavekktesla - 8 years ago
eq2675, could you pm me with your experience in this matter. I might have some info.
questions / discussions ...
eq2675 - 8 years ago
PM sent
christopherpfinch - 8 years ago
We just got hit yesterday by this from a ZIP file in our email.
We use a remote session for all users, so all virtual desktops reside on the same server. Only one profile has been infected on that server and the share drive on another server. The user has been logged out of their profile and the process is not running. Aside from that, all other servers and profiles are aces!
Things I've learned about our setup:
There are no backups
The system restore function on server 2008 R2 is nonexistent to my understanding.
They are asking for 7 bitcoins, so I'd like to not pay the money to get these files back.
Do I stand a chance?
Eshowers - 8 years ago
Just a heads up, this virus isn't strictly through emails. I have family members that picked it up by visiting a fake Microsoft website. They claim they didn't download anything and that Avast detected it as a possible fraudulent site; immediately after closing that security popup, the screen changed colors and the ransom message popped up.
I was skeptical since to my knowledge, most viruses need to be activated by executing or physically clicking on them.
Is it possible that this virus could infect a computer without directly downloading it?
Btw, they were searching for a tutorial on "microsoft word duplex printing." I attempted to search for the site, but didn't come across anything.
eq2675 - 8 years ago
Do you know what search engine they were using?
JoeyRG - 8 years ago
I am infected. Same story - just by browsing with Internet Explorer 9.
DanTheComputerMan - 8 years ago
Had a client get hit with this today. Luckily, had an up-to-date backup. Any word on whether the Cryptolocker Group Policy settings will prevent this variant?
kevinswan007 - 8 years ago
got 2 clients so far that got the locky ransomware. both paid the ransome. 1 was 3BTC, the other 0.5, very random! both time we got the unlocker file and got all the files back.
Both time got infected via email attachment. poor accounts ladies dont know any better.
for those who fear getting it while browsing, use ublock origin.
StEliosGR - 8 years ago
Also many of my customers infected. Im waiting for news!
Top22911 - 8 years ago
Will this virus also infect a system if the User is logged on as a 'User', 'Limited' or 'Standard User'? I'm looking for proactive ways as a system admin to prevent my Users from being infected other than explaining to them not opening e-mails or attachments or activating macros from unknown sources. What if macros are disabled on the workstations? Will the virus still active?
Lawrence Abrams - 8 years ago
Yes, ransomware typically runs under the security context of the user who installs it.
crisis2k - 8 years ago
Now Locky using ransomnote "_HELP_Instructions.txt" it seems like changed one.
That makes me so nervous.
dantelu - 8 years ago
I can recover the files! =D Takes quite a while tho. Depending on disk size.
Lawrence Abrams - 8 years ago
Care to share the method? If so, please pm me to discuss privately so the malware devs do not get wind of it.
Acevidal5 - 8 years ago
please dantelu can u PM me too as well i need to restore my files to be viewable again thank u
Kuetleong - 8 years ago
Hi Dantelu, can you share with me how you recover the encrpyted files? One of my company's PC is also hit with LOCKY thing!
Yaweza - 7 years ago
Can you please send me the solution as well. 1 of the computer has been affected by .locky virus. PLLEASE.
hawkeyez88 - 8 years ago
Yes please dantelu .. can you PM me as well? Nothing I've tried has worked to recover from this mess of an error.
Disabel - 8 years ago
Hello, i'm new here n got issue with this locky yesterday now i need help to recover my work file that has been encrypted. ==a
@dantelu, it would be great if you could PM me as well and share the method to recover the files
cesarfreitas - 8 years ago
Hey guys, can anyone help me with Shadow Explorer 0.9?
I was able to recover some files using Recuva and saved the files in a folder in the Desktop because, by default, we can't access System Volume Information folder, right?
Problem is, when I open Shadow Explorer, it only shows the C: drive dated 23/03... I recovered the files today... Where can I indicate this folder so Shadow Explorer can show me the files?
Or do I have to copy the files to System Volume Information manually?
Thanks in advance!
MrLateeBrown - 8 years ago
This is what was done to restore my clients files (steps down below)
I received a call from a client this morning (3/23/2016), mentioning all of his PDFs, Documents etc. on his Windows 7 Professional computer were all showing as LOCKY files, I mentioned that I hoped he didn't get hit by ransomware and that I would call him back to try to get connected to his computer.
I prayed and felt led to run 'System Restore', so I did and was surprised to see only one 'System Restore Point' when I was expecting multiple, however the one that was in there was labeled 'Automatic Restore Point' and dated 3/22/2016 12:00:03 AM, so I selected it and Restored.
After I got reconnected to the computer after the 'System Restore', it said it restored Successfully. I brought up the properties for his 'Desktop' folder, went to the 'Previous Versions' tab and it displayed 'no previous versions', I was like bummer. I brought up the Properties for some folders he had on his Desktop, went to the 'Previous Versions' tab and there were listings for 'Today' and 'Yesterday', I first checked out the one from 'Today' and sure enough, the files were changed to .LOCKY files. I opened 'Yesterday' and the files were unaffected. The date next to the folder displayed 3/22/2016 12:00 AM, when I compared this to the date on the .LOCKY files, they displayed a 'date modified' of 3/22/2016 around 3:55 PM and later. I eventually went back to the (C:) Drive, right-clicked on it and selected, 'Restore previous versions' (same as selecting 'Previous Versions' from the Properties view), there was a listing for the (C:) Drive for Yesterday with the date 3/22/2016 12:00 AM. I opened it and browsed through 'Users', 'Username' and when I saw the 'Desktop' was listed I was pleased, because several of the files needed were in the 'Desktop' folder. I closed the folder, canceled and went back to the C:\Users\Username right-clicked on the 'Desktop' folder and selected 'Restore previous versions' and was now seeing the listing for 'Yesterday', after verifying that the files from that date (Yesterday) were unaffected, I returned to the Properties view, selected the 'Desktop' folder from 'Yesterday' and selected the 'Restore' option and selected 'Restore' again on the confirmation window.
This is a Summary of what I felt led to do on this Windows 7 Professional Computer:
1) Ran 'System Restore' (Hold down the 'Windows key' R)
2) Type in: rstrui.exe and select OK
3) When the 'System Restore' window appears select Next, verify that you have at least one restore point, if you would like to ensure there are no other restore points, check the option 'Show more restore points'
4) I selected the only restore point I had: Date and Time: 2/22/2016 12:00:03 AM, Description: Automatic Restore Point, selected Next, Finish, Select Yes if you would like to continue.
5) After 'System Restore' has completed Successfully, close that message.
6) Select Start, Computer (For Windows 8 and later computers 'File Explorer' in the left pane select 'This PC')
7) In the top uppermost right corner you should see a 'Search' box, click in the box and type .locky
8) As it is searching, change the View to Details (You can press Alt V and select Details)
9) Add the 'Folder path' column (Right-click on the column names, More..., place a check in 'Folder path' and select OK, expand the 'Folder path' column out
10) After the search has completed, click on the 'Folder path' column to sort by it, do not close the search results window, you will need it later, take NOTE of the MAIN folders that were impacted. For example if you notice several of the .locky files in the following locations:
C:\Users\Username\Desktop
C:\Users\Username\My Document
C:\Users\Username\My Pictures
C:\Users\Username\My Music
Instead of taking a lot of time trying to restore each of the folders listed above, you could simply Restore the folder:
C:\Users\Username
I hope you understand the concept. If you have several files in the C:\ProgramData folder affected, and you choose to 'Restore' that folder, you might have to 'Skip' files that are in use by the OS or if you get Permission prompts. I might suggest enabling the option 'Repeat or Do this for the next ...' in the lower left corner of that dialog box.
11) So to 'Restore' a folder, navigate to the folder to be restored, right-click on it and select 'Restore previous versions', highlight the folder name that has a date prior to the affected files. For example the Username folder under 'Yesterday', select the 'Restore' option and selected 'Restore' again on the confirmation window.
12) After you have 'Restored' all of the main folders you took NOTE of from the search results window, now return to your search results, highlight a file name in the list, press Ctrl A (Edit, Select All), after all of the files are highlighted, deleted them.
13) In the 'Search' box type in: _HELP_instructions.txt, Select All on these files and delete them as well.
14) I world recommend clearing your 'Temporary Internet Files', I had noticed 'Security Risk' detections on the computer after we had restored our files.
After the cleanup I checked the HKEY_CURRENT_USER\Software key for Locky, but there was no Key there. I suspect running the 'System Restore', rolled the Registry back and that is why there was no entry.
Anyway, if this helps anyone, Thank God!
Happy Easter and God Bless!
cesarfreitas - 8 years ago
Hi MrLateeBrown, how are you?
In your case I might say you were lucky, because you actually had a restore point available.
In my case, the ransomware deleted all the restore points but one, dated after the infection. The first thing I tried when I got the computer was exactly that: check the C: drive for Previous Versions. But I couldn't find older restore points.
Anyway, thanks for the tips, this might help a lot of people if they come across the same problem, and with any valid restore point.
Happy Easter for you too!
cesarfreitas - 8 years ago
Oh wait, you did that after the System Restore?
But was the Restore Point after or before all was encrypted?
I didn't understand at first... I might try that now and see what happens, at least it's a good try.
Thank you!
MrLateeBrown - 8 years ago
After I assessed the damage, encryption took place 3/22/2016 around 3:55 PM and later according to the modified date on the encrypted files. I ran 'System Restore' restore point was specifically this: 3/22/2016 12:00:03 AM (So more than twelve hours before the encryption was run...
And Thanks for wishing me Happy Easter!
cesarfreitas - 8 years ago
Unfortunetly, that didn't work for me.
I checked the Previous Verison Files and all off them are already encrypted.
Well, Recuva was able to recover a few files, so I'm trying to recover the files using Shadow Explorer.
I'll post here if I have any news that might help people out there with this same problem...
MrLateeBrown - 8 years ago
Just so I am clear on what you are stating, this is a Yes/No question, you ran System Restore, and had no restore points prior to the encryption?
cesarfreitas - 8 years ago
Hi!
Yes, I ran System Restore and after that checked Previous Versions... It doesn't have older restore points.
The files Recuva restored were not enough too, so I'm trying other recovery softwares, but I'm almost giving up now... I think I won't be able to get all the files back.
At least they're not my files, I work as IT Support and one of the company's computer got infected... The user is not gonna be happy, but I made what I could...
Anyway, thank you for your help... I hope people can recover their files with this method.
Have a nice day!
MrLateeBrown - 8 years ago
That sucks, sorry to hear that! May the Lord make a way..
cesarfreitas - 8 years ago
Thank you!
Well, things like that happens sometimes... we gotta move on anyway.
zalbuu - 8 years ago
Any update on dantelu's solution; does it work? If so, could someone pm me the method?
pctechjbay - 8 years ago
I have had 5 computers with this virus on only one were the Shadow Volumes still intact and useable.
Stroler - 8 years ago
I used Recuva by PiriForm. Im sure it safe to say what was used, since if the locky devs would not want to destroy your hard drive. They want to keep everything intact so you pay up your Ransom. Luckely to destroy data from Hard drives(previous files versions etc) are a pain.
Locky also destroyed the clients Shadow copies. Some say....One can recover that but, Microsoft said even if you recover it, one cannot use it.
Stroler - 8 years ago
Edit: Recuva are able to scan for shadow copies that were lost and peek into them to get data back.
perritoxx - 8 years ago
i recovered the previous system snapshots deleted by locky,
can i ask how did you do it to explore the recovered system snap shots?
i put the files in the system folder but shadow explorer or system previous version just do not show the file....
thanks
superzareth - 8 years ago
"i recovered the previous system snapshots deleted by locky,
can i ask how did you do it to explore the recovered system snap shots?
i put the files in the system folder but shadow explorer or system previous version just do not show the file....
thanks"
1, to get restore with getdataback the files >1GB but how to restore, windows7 x32
thanks for your help!
cira529 - 8 years ago
I have problem with Locky virus.
Can someone explain me How is it possible to recover files with Shadow copies or Recuva or any other recovery solution, after they were encrypted and deleted, one after one?
It is very big chance that "new encrypted file" will be written over some other "old deleted file" that we want to recover.
mirusev - 8 years ago
It hugely depends on disk usage, make your try...
mirusev - 8 years ago
once it happens... make me to think, is not the locky spread by backup companies? :(
cira529 - 8 years ago
Thanks mirusev.
I will try and make everyone here know results of recovery process.
It is very possible to be truth but also very possible to never find out what is happening...:(
mirusev - 8 years ago
Wish you 100% restore!
and like me, think about a backup... now struggling with iDrive, desperate speed :( at excellent price, but still desperate
any experience is welcome (about other backups)
dmilton - 8 years ago
Locky and Google Drive:
I'm attempting to support a family member who opened an attachment that appeared as an an invoice sent to him in his role as treasurer for his church from his church's email account. He was keeping his files in a Google Sync folder so that he would have a cloud backup. Fortunately, he realized what was happening and shut down his computer before it had completed encrypting everything. Logging into his Google Drive from another computer, we found that some files were renamed but not encrypted. Many were encrypted.
Here's the important news:
1. All prior versions of the encrypted and/or renamed files on Google were gone.
2. The prior versions were not in trash and Google support reports that (2 days after infection):
a) No files were logged as deleted from the account in the last 25 days
b) The prior version of the files no longer exist,
c) There is no way to roll back a Google Drive account to a prior time point
d) The .locky file extension cannot be changed even by Google.
This is my first post here. I'm a biomedical physician scientist with a modest, mostly statistical, programming background and my relative is a retired chemical engineer.
I saw someone on this site mention recovering from Dropbox. Were those files synced to Dropbox or put there and accessed only via a browser interface? Are other cloud services (iCloud, OneDrive, Box, Dropbox, ...) vulnerable? Does anyone know how Locky accomplished this feat?
Regard
Joe_BubbA - 8 years ago
That's very strange. GD has 30-day versioning, doesn't it? Were none of the files on the drive updated in the last 30 days prior to the Locky attack?
dmilton - 8 years ago
Yes GD says it keeps versions for 30 days, but there were no previous versions and GD support has no explanation for why there is not at least one version -- even for files that had not been changed recently there should be the version before the name was changed and contents encrypted. But no, there is not -- and even GD admin seems unable to remove the .locky file ext.
MrLateeBrown - 8 years ago
dmilton, if you don't mind me asking, yes or no, have you performed the following steps on the computer yet?
1) 'Windows key' R)
2) Type in: rstrui.exe and select OK
3) When the 'System Restore' window appears select Next, verify that you have at least one restore point, if you would like to ensure there are no other restore points, check the option 'Show more restore points'
dmilton - 8 years ago
"dmilton, if you don't mind me asking, yes or no, have you performed the following steps on the computer yet?
1) 'Windows key' R) ..."
Dad's been doing something -- not clear yet what.
MrLateeBrown - 8 years ago
If you haven't already, you might remote connect to your Dad's computer, TeamViewer (teamviewer.com) has a free client that both of you can go to the site, download the latest version, after you finish the install (their is a 'run one time only' option), it will give you both a ID, you put in his ID and call his computer, viola..
mirusev - 8 years ago
Sorry to hear that, but how it is possible, dmilton???
I've personally restored part of my data exactly via Google drive, all previous versions are there, just an issue with the names. And yes, I do confirm - they are not deleted, they are encrypted and renamed, but the unencrypted files are there as "non-google files". They keep up to 100 versions unless you check "keep forever" - then they keep 200 versions of the file. Even not asking the support for help - they are just there...
It is same for Dropbox.
Another story are backup companies, like iDrive for example - the restore success depends on how good and how frequently the backups are done. But for example, backing up 350 GB on iDrive, started 4 days ago, resulted only 37 GB for the time being. It just upload at 1-2 Mbps speed (aka 100-200 KB/s) which is terrible. So, for that initial backup of 350 GB it will need about 40 days...
dmilton - 8 years ago
Certainly one can restore to older versions, if some malware has not deleted them. But, this is very different.
Natrat22 - 7 years ago
FYI I can answer this re dropbox. The ransomware my client got changed the filenames and added .encrypted on the end. This immediately means there are no "Revisions" to revert to for any particular file on Dropbox, or Google Drive. They see it as a brand new file.
Dropbox however does log the filename change as a Deletion Event. By contacting Dropbox support and providing the link to the deletion event (where 25000 client docs were encrypted in dropbox - can can see this in the Events section on the Dropbox website) they were able to revert the entire Dropbox to the point just before that deletion event, restoring everything.
People seem to be suggesting Google Drive doesnt work this way?
Even the Dropbox method is annoying as it requires Dropbox Support intervention. With the time difference in Australia back and forth emails took 2 days for them to action it.
If you jsut need cloud backup, i'd go with something you can manage 100% yourself and restore revisions without needing to contact support. I use Crashplan for this, i've recovered half a dozen ransomware infections using it.
cheers
nathan
mirusev - 7 years ago
I've personally saved the files thanks to Gdrive... Can not agree that "This immediately means there are no "Revisions"" is a true. Can not add screenshots because the right files are current versions in Gdrive and the other versions (.locky) are already deleted. Just do not understand how and why Gdrive has different behavior, but for sure it works for me. In other post already said what is the main drawback - missing folder's versioning which makes a lot manually restoring thousands of files which takes days. But the files are saved at the end of the day... by Gdrive
mirusev - 7 years ago
here is an example, a txt file, which was renamed many times, and simulating encryption - the text inside it was changed many times as well
http://screencast.com/t/D1DWVZQ4F
MrLateeBrown - 8 years ago
I replied to 'dmiltons' post
Saga Lout - 8 years ago
The varierty my customer invited in (stupidity) and had no backup (they didn't know the machine had to be switched on and running on the scheduled time of the 1st of each month at 19:00 - doubly stupid) wiped out all prior Restore Points. The only one available when I got the machine was as Automatic one time-stamped 01:14:07 on that day - a time when the machine wasn't even turned on.
I've tried everything to restore the files and made three attempts through TOR to get to their site but failed every time.
My question is has anyone apart from one poster above paid them and actually got a working decryption key back? My customer would stump up half a Bitcoin at £148 GBP only if they were certain of a positive result but wouldn't go as far as 3 Bitcoins.
banuazizi - 8 years ago
OK So it says here that files and folders containing these words are ignored.
tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows
How about putting all your movies, mp3, photos, documents etc onto folders called temp, can anyone verify that they are left intact ?
at the moment i'm running two apps: http://www.majorgeeks.com/mg/getmirror/bitdefender_anti_ransomware,1.html
and
http://www.majorgeeks.com/mg/getmirror/malwarebytes_anti_ransomware,1.html
along with ESET AV, might be good idea to run them two.
Saga Lout - 8 years ago
Too late for me to test that one for you because the machine has gone back to its owner. I thought they might have targetted certain filename extensions wherever they were stored.
Prevention is always better than cure but education on how to deal with e-mail is paramount here. My website is hosted in the States so I get 200 Spam on average a day from myself, forwarded to safer accounts over here. There is a long list of tempting words that appear in the subject line and its easy to see how people get hooked but they must learn extreme caution and even if they open a mail, don't download any attachments and definitely do NOT click on live URL links.
cesarfreitas - 8 years ago
Here at work, it's incredible how people ignore our instructions.
We've had a lot of spams incoming, and I sent everybody an e-mail informing that, whenever they receive an e-mail with attachments, even if received from a known e-mail, people should call us (IT Support) to check the attachment before opening it.
Then people call sayind they tried to open but nothing happened and the file was empty... Guess what happened after that?
People just open all attachments like it's simple and safe. I agree with you, education is a good prevention too, besides antivirus or other tools.
Lester Ingber - 8 years ago
Does OneDrive (not) work like GDrive? That is, if files are being backed up into OneDrive cloud, and then ransomware strikes, don't you still have the old versions available (different names, bytes, ?) for recovery?
dmilton - 8 years ago
An update on Dad's situation: He did the recover (but not holding down the win key). His system drive was restored to a recent point before the attack. But, his data drive (D:) was grayed out and not available to restore.
As for vulnerability of OneDrive and other cloud services -- I don't know because figuring out how this exploit worked is well beyond my meager skill set. But, I suspect that if GD is vulnerable the others are as well -- although there may need to be some customization of the malware for each cloud drive vendor.
MrLateeBrown - 8 years ago
dmilton, Praise God that your Dad was able to restore to System Restore Point before the attack. Did he also have his 'My Documents' folder on his (D:) drive as well? If so, that sucks!
It seems that Windows 7 and later by default only configure the drive that the OS is on. If anyone wants to protect additional drives on the computer, they have to configure them to be protected. To do so on Non-Server OS's Windows XP through Windows 10, do this:
1) 'Windows key' (plus) R
2) Type in: control sysdm.cpl and select OK
3) Go to the 'System Protection' tab ('System Restore' in XP)
4) In the area where you see 'Available Drives' select the additional drive you would like to protect and select 'Configure' ('Settings' in XP, in Vista, simply place a check in the box to protect it; Vista will use up to 15% of total disk space)
5) Enable Protection/Monitoring for the drive and adjust the 'Disk Space Usage' and select OK (if you would like to protect additional drives repeat steps 4 & 5 on those drives)
6) Select OK
Hope this info is helpful!
mirusev - 8 years ago
I still do not understand how the GDrive failed, but after the hit it saved me. I started searching for a backup solution, stress tested GDrive again and got iDrive and stress tested it as well. Both would survive on ransomware attack! Slightly better is iDrive because you may restore versions per folder against only per file on GDrive which is huge win with thousands of files. But iDrive gives 1 Mbps per task, which is terrible. I have to split on 15 parts my 350 GB, to may get 15 Mbps upload and still over a week is needed for the initial backup.
Joe_BubbA - 8 years ago
Even though most cloud storage/sync solutions provided versioning, it may be worthwhile to consider disabling sync (or setting the service to not start when Windows starts) and then just running the app/enabling sync as needed to update any changes you've made. This should prevent any Locky encrypted files from being synced to the cloud should you become infected. Make sense?
mirusev - 8 years ago
yes, it makes... but leave it to no-automation and it will fail, just imho
mirusev - 8 years ago
action (versioning) per folder, as in iDrive is just perfect, if the upload speed was more, I would say: it is best prevention to no matter what virus....
I have Qnap NAS 3TB, mirroring disks and thought it is a solution, but no other solution than BACKUP, end of story! :)
(I would probably get second NAS to makes backups of the first, and the second will be backup-ed to the cloud). In that scenario the lost of data could be only if the two NASes are dead and the cloud backup is attacked, hacked, bankrupted - all of that at exactly same moment.
BlazeAxtrius - 8 years ago
If I put all my files in a folder named Program Files (x86) or Windows will the Locky virus just skip them and not encrypt anything in the folder?
For example if I have C:\All files\Program Files (x86). Will it just skip through them and not touch them. So I practically have a back up on the same computer that the Locky can't encrypt.
Also I found some Bitdefender Anti-ransomware. Does that actually work and stop the virus if it is started?
mirusev - 8 years ago
If it does the trick, it would be until next locky... So, think at larger view, or at least I try to do it :)
btw, installed the same anti-, but for sure it will be bypassed, even by person like me, mean - little knowledge in programming
ImranTahir - 8 years ago
Unfortunately, there are no easy shortcuts to get data back encrypted by .locky Russian ransomware
but if you are dying to get back your data, can contact for solution
Demonslay335 - 8 years ago
Are you offering a real solution to decrypt files? Would you be available to discuss further via PM or email? No matter the difficulty, if there is a possible way for actual decryption, I am willing to pursue it on behalf of helping the community. Afraid I don't dial international numbers from another country.
ImranTahir - 8 years ago
I am professional and expert, you may contact in any type of decryption, I m offering a real solution only for those persons they can;t survive without files
Lawrence Abrams - 8 years ago
Imran, we only people to offer services if they have been discussed with me about their methods and what they can actually achieve. Not that you are one, but too many scammers out there. I have removed your contact info and if you want to private message me more info about your methods I can determine if this is something I would allow.
ImranTahir - 8 years ago
<p>Dear Grinler as already discussed, I have solution and can show you my skills but I am sorry I can't share all procedure, but in your respect I can say that I have figure it out and can help people. if you are still not agreed as people are lost hope, you can send an infected disk image and I'll show your files.</p>
Lawrence Abrams - 8 years ago
Once again, this is not good enough. You can contact me privately to discuss, but I cant allow you to promote your services without having a bit more information. We have had too many scammers in the past offer services to find they couldn't do what they promised.
ImranTahir - 8 years ago
Dear All,
This document has some important information about computer infection that rename all your important files so that they have the extension. Locky (locky is the nick name of Russian ransomware creator Crook rocky)
o The most common way that Locky arrives is email
o You receive an email containing an attached word document
o The document looks like gobbledygook/ rubbish
o The document advises you to enable macros “if the data encoding is incorrect.”
o If you enable macros, you run code inside the document that saves a file to disk and runs it.
o The saved file serves as a downloader, which fetches the final malware payload
o The final payload could be anything, but in this case is usually install the Locky Ransomware
o Locky scrambles all files that match a long list of extensions, including videos, images, source
o Locky also removes any Volume Snapshot Service files
o Unfortunately, there are no easy shortcuts to get data back if user don’t have a recent backup
o Backup regularly and keep a recent backup copy off-site.
o Be careful about unwanted attachments and unknown sender.
o Don’t give yourself more login power than you need, only login with admin powers when really need and logoff as soon as you don’t.
o Don’t enable macros in document attachments received via email, consider installing the Microsoft Office viewers, viewer applications let you see what documents look like without opening them so you can’t enable macros by mistake
CAUTION!
It can affect any files in any directory on any mounted drive that it can access, including removable drives that are plugged in at the time, or network shares that are accessible, including servers and other people’s computers, whether they are running Windows, OS X or Linux. If you are logged in as a domain administrator and get hit by ransomware, it could do very widespread damage
Saga Lout - 8 years ago
There's nothing in your list that most folks will already know but for the few who are affected, such as my customer, it's too late when the devastation has already taken place. If your list prevents one person from falling for this scam in the future, it would be worth keeping here but your claim to have a method of restoring the files is highly questionable.
In another Forum where I have Moderator facilities, I would have pulled your post with the phone number and I'm surprised it has remained here for so long.
ImranTahir - 8 years ago
I got this issue (locky ransamware) last month and sorted out the solution
I have answers for your questions and that is challenge, even if a user has deleted partition, reinstall his system and still willing to get back the stuff :)
can contact
ImranTahir - 8 years ago
And, as you can read in my post, this solution is only of willing persons they can;t survive and dying to get files
Roby24 - 8 years ago
Hi, are we any closer in finding a way of recovering the files besides reverting to a backup/restore method? I recall Teslacrypt eventually had a recovery tool that could decrypted the files. I think a similar method could do the trick in the future but without knowing much about Locky it makes it more difficult!
In addition when Cryptolocker V1 was out I recall an organisation managed to access the cypto-gangsters servers and users where able to recover data via inputting a certain set of information onto a web portal. Apologies for the long message I am new to posting but I seen almost all the various revisions of this twisted "product" due to my job role.
Thanks Guys! Hopefully we can beat LOCKY!!
ImranTahir - 8 years ago
Roby can you help me to unlock the Cryptolocker V1, I need your help to get infected system
Thanks
IT
cesarfreitas - 8 years ago
I've read so many comments but I can't remember one thing, can anybody help me?
After all the infection and the files encrypted, is it necessary to remove the virus?
I would prefer to format it (after backup) but my client doesn't want to.
Will it encrypt any future files?
Thanks!
mirusev - 8 years ago
I think (but only think) that it self removes. A format is a must imho. And there is a tool which fool it that the machine is already infected (i doubt that in future versions of the virus it will work)
cesarfreitas - 8 years ago
Thank you!
But I think formating is the best option...
mirusev - 8 years ago
I agree!
ImranTahir - 8 years ago
cesarfreitas, I can help to get files back, can you send the drive?
k-gsp - 7 years ago
ImranTahir, please, can you help me to get my files back?
ImranTahir - 7 years ago
yes, can try to get files but depend on conditions
k-gsp - 7 years ago
Thank you, ImranTahir. Could yo tell me what conditions, please?
mirusev - 7 years ago
scroll to the bottom, please, check your files
carllo - 7 years ago
Imran, could you help me with LOCKY files?
rheyden1 - 8 years ago
If anyone was able to decrypt a locky file, please PM me. I've tried just about everything and would really appreciate some help.
santare - 8 years ago
Regarding ransomware, locky in this case:
If you connect to the TOR site, can't the FBI have a look at who owns the server (skip the Apple/FBI affair), seize the server and get the files back. TOR is not gonna tell them because
of privacy issues. We can force that, but you can see who is the owner of the ransomware servers and arrest the people.
Now, this is where I see difficulties (agree to disagree in advance).
1.Anything online related sparks an outrage (ie FBI arrests a hacker instead of banker), nobody wants their internet taken away
2. Proving the server is intended for ransomware is difficult at best
3. Finding a script for ransomware, which can be the same as lock my files shareware, which
you can control.
4. Ransomware should be prosecuted as blackmail, but it can't be, because it didn't happen
in real life.
mirusev - 8 years ago
About 4, you are wrong, it is a blackmail. Unfortunately the previous 3 points are near to impossible or just impossible :( You should take a deeper look about TOR network.
santare - 8 years ago
I know you can't get who.is on TOR websites, but I think you can force as an FBI to
hand over the server information. Regarding point 4, what I meant with blackmail, it can't
be prosecuted, because it didn't happen in the real world, but happened in the cyber world.
And cybercrime usually goes unpunished.
mirusev - 7 years ago
IMPORTANT! It is realllyyyy important :)
I've found that the virus may have a bug or just not enough time but anyway, so now the good part. Based on my files results I may say that it encrypted no more than 5% of all. So, it firstly rename - there it has much success - almost 100%, but it then starts to encrypt. So, in short - check your files and if you may guess what type of files are they - try with the appropriate application. Guess by file location and by files size...
Be sure that the virus is removed first!
Am pretty sure that was the solution by ImranTahir...
mirusev - 7 years ago
one may open any file with notepad (or I do using notepad ). Now I try with JPG: it starts with "яШябvExif MM" these symbols, pay attention on Exif - so such file should be JPG or other image file.
GIFF starts with "GIF89aр А "
PDF starts with "%PDF-1.7"
blank XLSX "PK"
I hope you got the idea
Saga Lout - 7 years ago
Sadly the long arm of the law, including your FBI, doesn't stretch into Russia where these extortionists are.
mcerdem - 7 years ago
Good morning,
Unfortunately my files are encrypted by Locky Extension, i have uploaded one encrypted file with ransomnotes (html and jpeg files) on attachment, if you can help me i will be highly appreciated.
https://www.sendspace.com/file/5qdlqk
Thanks in advance.
Best Regards.
Cihan
crisis2k - 7 years ago
Cihan hi. i know who you are.
I have been knew you are one of the analysers.
And also you have infected by locky?
mcerdem - 7 years ago
"Cihan hi. i know who you are.
I have been knew you are one of the analysers.
And also you have infected by locky?"
thanks yes its me, its not me, one of my friends unfortunately..
mirusev - 7 years ago
The point was, that even renamed, files could be unencrypted. Thus, do not mislead by name and to check the files. That one is really encrypted, unfortunately
carllo - 7 years ago
hello, I´m having the same problem with the LOCKY ransomware. I was able to get the public key by regedit. Is there some way I can use this key to decrypt the files?
LogicEE - 7 years ago
I wrote a little program that will go through your outlook emails and check for macros in word, pp, and excel documents, I have been using it at work, had a few computers infected with this virus. figured i would share!
Let me know if anyone wants source code.
https://drive.google.com/file/d/0B19xgNwSyIP5SEtJOGluV0FxaXc/view?usp=sharing (Find Emils with Macros)
mirusev - 7 years ago
Is it for specific office?
valent_svk - 7 years ago
Hello. My computer was inficated by locky virus too. All my doc xls xml files was encripted.
My problem solved by using the ShadowExplorer program.
(link: http://malwarefixes.com/remove-locky-ransomware-and-decrypt-files/ !!!!option 2!!!!!!)
(link to download: http://www.shadowexplorer.com/downloads.html click latest version)
After easy installing you can find directory or files which was infected and simply restore to previous version
I tried already option 1 and searching resolving on internet but no success. ShadowExplorer helped me... YEAH!
Lawrence Abrams - 7 years ago
Yes, Locky sometimes fails in deleting the shadow volume copies. As described here:
https://www.bleepingcomputer.com/virus-removal/locky-ransomware-information-help#restore
ChiefTech - 7 years ago
Yeah. I just had a clients PC come in with this and it had failed at removing the shadow copies. I used ShadowExplorer to export his data and backed it all up. Then I continued with a system restore. It's seems it's pretty common for it to not remove the shadow copies so there may be some luck in store for you guys out there!
Joseph75 - 7 years ago
Hi OK so had a problem with this locky.... encrypted a few of my files mostly excel and word but left jpg and pdf alone. Found the _HELP_instructions file and went to see what the russians wanted for ransom but the site been shut down now. Good. But after looking a bit further this thing has spread to all the mapped drives i had access to including NAS drives. Nasty Nasty thing. But after some snooping around i think i have actually found the .exe that caused the whole thing to happen. Dont suppose there any way this could be reversed to find out if i can get a couple of files back that missed the backup ? Its an exe file not the email part so i think its the downloader file. Anyone know what to do with this exe file to hack it back ? It is russian for sure.............. 113kb
MrLateeBrown - 7 years ago
Have you tried running 'Windows System Restore (Windows key {plus} R > rstrui.exe > OK) yet'? After you restore to the Restore point before the attack, you should be able to go into the properties for the folder and see the 'Previous Versions (Restore previous versions)'
Joseph75 - 7 years ago
Hi yes but there no option for that on my NAS drives where the files lived on a mapped drive. This is my biggest problem.
I know i need to move forward and forget about my lost files but i know there will be a fix at some time for this. Whats best for potential recovery ? Should I disc image the PC so any "key" files will remain incase they are needed to run a fix ? Im pretty sure that there are hidden keys on the computer that would be needed for a fix ? Any helpers ...........
iqra96645 - 7 years ago
Imran please help me in any condition iqra96645@gmail.com
locky ruined all my memories
thx plz
mcerdem - 7 years ago
dear all, please be careful and do not let "Imrantahir" to connect your computer, he can not decrypt your files but he can damage to your other files, around 1 month ago, i did let him to connect my computer but he deleted my windows user and created new one as IT with new password, fortunately i have backed up my all files and cracked the password of his new windows user, so i advice you to be carefull...
Saga Lout - 7 years ago
"dear all, please be careful and do not let "Imrantahir" to connect your computer, he can not decrypt your files but he can damage to your other files, around 1 month ago, i did let him to connect my computer but he deleted my windows user and created new one as IT with new password, fortunately i have backed up my all files and cracked the password of his new windows user, so i advice you to be carefull..."
I hate to say this but I warned about that character way back. I just wish the Forum Mods had taken his rubbish down.
Today00 - 7 years ago
Please send file invoice_J-17105013.doc to me for studies .
Send to my email. AtimeBtime@outlook.co.th
the doctor - 7 years ago
Hi, this is a work in progress. I am working on a group that has 9 workstations and a server.Locky has infected most of the workstations. and the server. The server's backup is also infected. Is there a way to manually remove the ransomware? If not, then I will have to totally clean and reload Windows and Office on each computer.
Lawrence Abrams - 7 years ago
Locky typically encrypts a computer and then removes itself. There usually is nothing malicious left behind. With that said, if Locky was installed via a exploit kit, it is always possible that other malware was installed as well.
The truly only way to know if a computer is clean is to reinstall, but I know many people who are affected by Locky and do not reinstall. Have you performed a few scans to see if anything was left over and detected?
cesarfreitas - 7 years ago
Good morning guys!
Any news on a .locky decryptor yet?
I've been away for a few time now and I'm not sure about it...
Thanks
Lawrence Abrams - 7 years ago
Unfortunately, not yet.
cesarfreitas - 7 years ago
Thank you, Grinler.
Badrans - 7 years ago
Hi guys!
Any news on a .locky decryptor yet?
Thanks
Norman_Wallace - 7 years ago
Here is a ransomware removal tool:
I hear it removes the most of the latest ransomware including Locky!
32-Bit Download: https://www.sendspace.com/file/asox9e
64-Bit Download: https://www.sendspace.com/file/dvtys1
Password: rcleaner
Scans clean with virustotal.com
Mr.Tom - 7 years ago
Doesn't scan clean anymore..
https://virustotal.com/en/file/9ec495fa86410a72a6bd17ed23d45d1aaa35a6ae5e46352764cf10c754f7201d/analysis/1475085232/
Mr.Tom - 7 years ago
A company I deal with just got hit by this .ODIN variant.
https://www.bleepingcomputer.com/news/security/locky-ransomware-now-uses-the-odin-extension-for-encrypted-files/
Locky got too greedy and asked for 3.0 bitcoins. My customer was outraged and is NOT going to pay that much. Instead they're buying a new computer today and going to reinstall one needed program from a 2 week old backup and enter the rest by hand. So they'll ultimately be paying a little under $1K w/repair fees. A lot better than $2K repairs.
Let that be a lesson to would-be ransomers..
Lawrence Abrams - 7 years ago
Yes, the ODIN variant is all we will be seeing from this point forward.
It is also suspected that the ransomware will examine various settings/features of the computer that it is installed on and display a higher ransom amount for those who are in a workplace environment.
Saga Lout - 7 years ago
Does that mean Zepto is out of fashion already? I was called out to one only two days ago.
Lawrence Abrams - 7 years ago
Yup, Locky switched to the Odin extension. Zepto is shelved at this point.
Mr.Tom - 7 years ago
I suppose since they seem to be sending these out through emails they can change versions on the fly. I just got some emails yesterday on two different addresses. The usual phishing scam. One said my card had been declined and they tried to get me to open the .zip attachment. Phat chance on that one. I get so few emails that it's easy to focus on what I'm viewing.
People just need to slow down and think about what they're going to do and determine if they really need to do it. I can't tell you how many people actually fall for the webpage support scam and actually call the phone number that it tells them to call. And then most of the time they follow the scammers orders and type in a command and give them remote control of their computer. Then they either give them their credit card number or if they don't their computer gets a password.
manestevez - 7 years ago
BACKUP BACKUP BACKUP ... and BAKCUP
But good backup .
every day I get people to decrypt. I always tell them: from now sure you will have a good backup system.
to decrypt: the only solution is to pay the hacker. (I am sorry).
There are some specific cases if they can be decrypted without paying the hacker, but very few cases.
manolo@controlip.net
Saga Lout - 7 years ago
If only I could believe they're going to give you a decryption key once they've got the money, Manolo.
It would help to put an end to this if television programmes were clearer about how easy it is to be conned in this way. This should be on the main News broadcast of the day in every country and at least once a month.
A lot of folks depend on the Microsoft scheduled backup but I've come across many instances where it's failed.
SleudianFrip - 7 years ago
My company just got hit by this...at least something similar. One of our employees opened an email attachment. It was a zip file with a .WSF file. It is a Locky variant but all files are encrypted with a .THOR file extension. Unlucky for us this employee had many mapped network drives and it just obliterated hundreds of thousands of files. Lucky for us it is all backed up!