
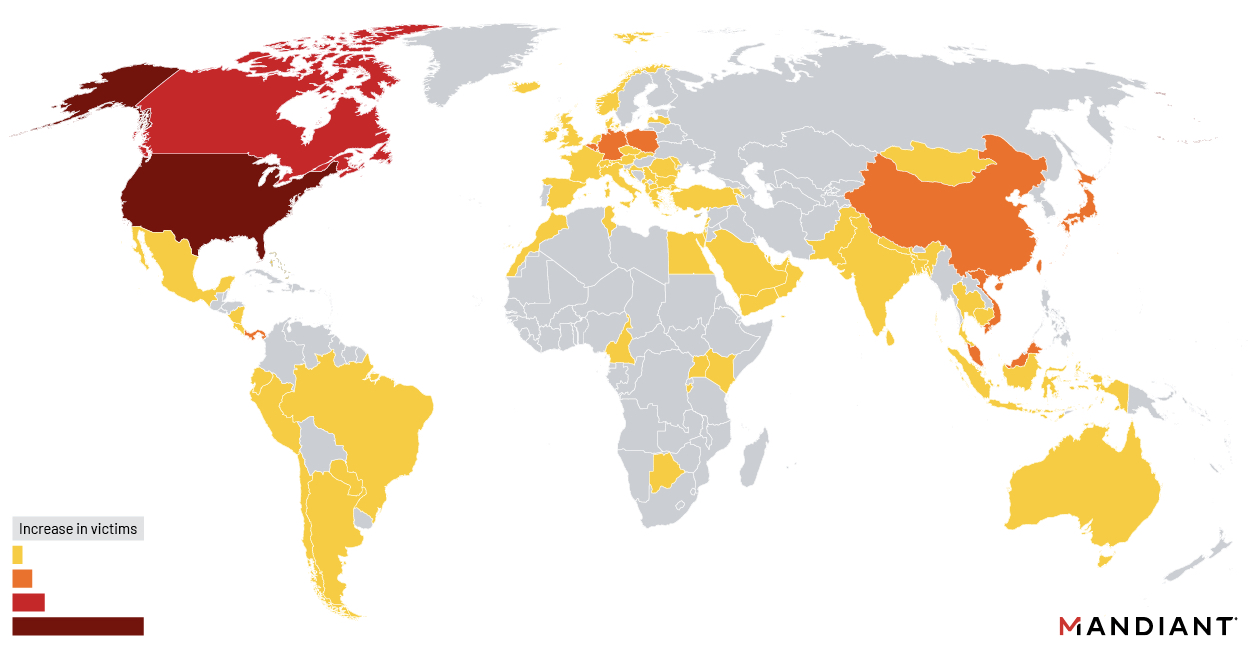
Suspected Chinese hackers disproportionately targeted and breached government and government-linked organizations worldwide in recent attacks targeting a Barracuda Email Security Gateway (ESG) zero-day, with a focus on entities across the Americas.
Almost a third of appliances hacked in this campaign belonged to government agencies, most of them between October and December 2022, according to a Mandiant report published today.
"Notably, among North American identified affected organizations, there were numerous state, provincial, county, tribal, city, and town offices that were targeted in this campaign," Mandiant said.
"While overall local government targeting comprises just under seven percent of all identified affected organizations, this statistic increases to nearly seventeen percent when compared to U.S.-based targeting alone."
The attacks' motivation was espionage, with the threat actor (tracked as UNC4841) engaging in targeted exfiltration from systems belonging to high-profile users in government and high-tech verticals.
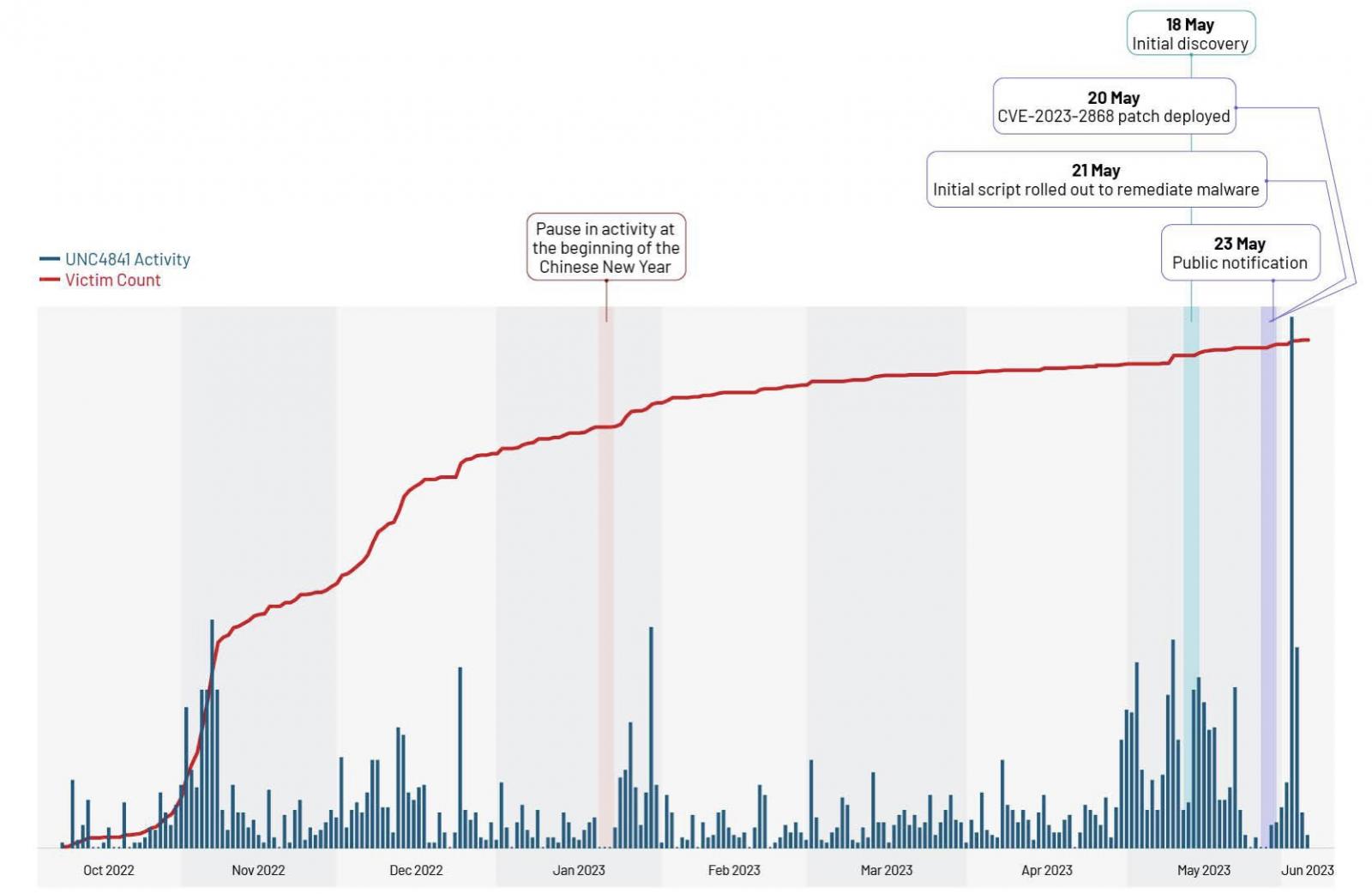
Barracuda warned customers that the vulnerability was being exploited to breach ESG appliances on May 20, when it also patched all vulnerable devices remotely.
Ten days later, the company also revealed that the zero-day bug had been abused in attacks for at least seven months, since at least October 2022, to drop previously unknown malware and steal data from compromised systems.
Customers were warned one week later that they must replace hacked appliances immediately, even those already patched (roughly 5% of all ESG appliances were breached in the attacks, according to Mandiant).
The attackers deployed previously unknown malware, including SeaSpy and Saltwater, and a malicious tool, SeaSide, to gain remote access to compromised systems via reverse shells.
CISA also shared details on Submarine (aka DepthCharge) and Whirlpool malware that was deployed in the same attacks as later-stage payloads to maintain persistence after Barracuda's May 20 advisory onto a small number of previously compromised devices belonging to what Mandiant believes were high-value targets.
This "suggests that despite this operation's global coverage, it was not opportunistic, and that UNC4841 had adequate planning and funding to anticipate and prepare for contingencies that could potentially disrupt their access to target networks," Mandiant said in today's report.
"We're contending with formidable adversaries that boast vast resources, funding, and the know-how to successfully execute global espionage campaigns undetected. China-nexus espionage actors are improving their operations to be more impactful, stealthy, and effective," Austin Larsen, Mandiant Senior Incident Response Consultant, told BleepingComputer.
FBI: Barracuda ESG appliances still under fire
While Mandiant and Barracuda are yet to find evidence of new ESG appliances being compromised via CVE-2023-2868 exploits after they were patched, the FBI warned last week that the patches are "ineffective," and that patched devices are still being compromised in ongoing attacks.
The U.S. federal law enforcement agency also reinforced Barracuda's warning to customers that they should isolate and replace hacked appliances as soon as possible, advised them to investigate their networks for potential breaches, and urged them to revoke and rotate enterprise-privileged credentials (e.g., Active Directory) to thwart the attackers' attempts to maintain network persistence.
"The FBI continues to observe active intrusions and considers all affected Barracuda ESG appliances to be compromised and vulnerable to this exploit," the agency said.
"The FBI has independently verified that all exploited ESG appliances, even those with patches pushed out by Barracuda, remain at risk for continued computer network compromise from suspected PRC cyber actors exploiting this vulnerability."
Barracuda's security products are used by more than 200,000 organizations worldwide, including government entities and high-profile companies.


Comments
Mahhn - 7 months ago
I have to wonder when these preludes to war will no longer be preludes.
AutomaticJack - 7 months ago
"I have to wonder when these preludes to war will no longer be preludes. "
Agreed. Cyberwar has been waged for a long time now, but these pokey attacks have been escalating it seems. Really start to worry when state actors start to disable critical infrastructure of major powers, next stop is typically kinetic war.